From Detection to Prediction
Leveraging AI for Proactive IT & Cyber Resilience
Introduction:
Why Reactive is No Longer Enough
In the modern digital era, IT infrastructures are evolving rapidly—so are cyber threats and system failures. Businesses that continue to rely on reactive security models risk falling behind or worse—experiencing devastating outages or breaches.
To stay ahead, organizations must embrace AI-powered predictive monitoring and cybersecurity. At IOTA Solutions, we lead this transformation with a unified suite of tools:
- Trace9® – AI-driven IT monitoring
- Amygdala XDR® – Advanced threat detection and correlation
- iNAC® – Intelligent network access control
Together, these tools help businesses move from detection to prediction, reducing downtime, improving security posture, and driving operational efficiency.
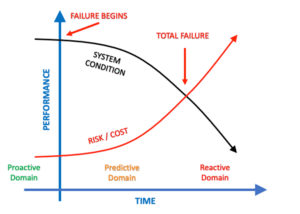
Why Prediction is a Game-Changer
Imagine being able to prevent:
- A disk failure before it affects users
- A DDoS attack before it overwhelms your servers
- A privilege escalation before credentials are exploited
That’s the power of prediction—and the value of AI-driven observability and security. By analyzing data in real-time, predictive systems spot anomalies and trends that traditional tools miss.
Key Benefits:
- Reduced Mean Time to Resolve (MTTR)
- Fewer successful attacks & breaches
- Lower operational cost through automation
- Smoother performance & happier end-users
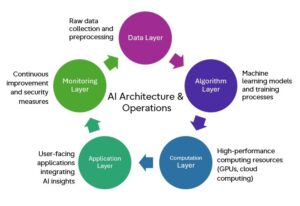
The Role of AI in IT & Cyber Resilience
Artificial Intelligence enables machines to learn patterns, identify risks, and trigger intelligent actions. At IOTA Solutions, AI forms the backbone of all our tools:
- Trace9: Predictive Monitoring Engine
- Continuously baselines resource consumption (CPU, memory, disk I/O)
- Detects slow-developing anomalies across distributed infrastructure
- Notifies teams before degradation impacts services
- Amygdala XDR: Threat Prediction
- Correlates logs and user behavior in real-time
- Identify pre-attack indicators using AI/ML
- Prioritizes alerts based on impact, context, and kill-chain progression
- iNAC: Intelligent Access Control
- Builds behavioral profiles of devices/users across the network
- Flags and blocks anomalous connections—even from “trusted” entities
- Integrates with Trace9 for telemetry-based policy enforcement
Real-World Impact: Proactive in Action
- One of our enterprise clients deployed Trace9 across 120+ production nodes. Within weeks:
- It predicted a major disk failure 2 days before actual impact.
- Their ops team replaced the disk without any downtime.
- Amygdala later prevented lateral movement during a brute-force attempt—detected due to a rare login time pattern.
- With predictive alerting, this client saw a 30% drop in unplanned outages and reduced incident response time by 40%.
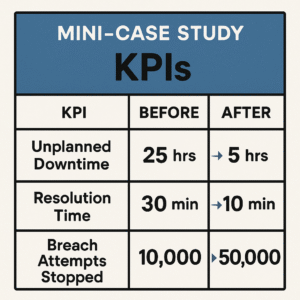
Block with before/after KPIs (unplanned downtime, resolution time, breach attempts stopped)
Getting Started with Predictive IT Monitoring
- Step 1: Baseline Your Environment
- Map your critical assets, SLAs, known failure points.
- Step 2: Deploy Trace9 + Amygdala + iNAC
- Use modular rollout per function (monitoring, XDR, access control)
- Step 3: Automate Remediation
- Set smart rules: quarantine, auto-throttle, user-block, patch alerts.
- Step 4: Continuously Train the Models
- Feed alert outcomes and system changes into your AI models.
The Future Is Predictive—Join the Movement
The digital battleground is expanding—but so is your ability to prepare.
With Trace9, Amygdala XDR, and iNAC, you don’t just defend—you anticipate. This proactive approach to IT and cybersecurity is no longer a luxury; it’s the new baseline for resilient businesses.
Author: Awais Javed