Introduction
In today’s digital landscape, perimeter-based security is no longer enough. Modern cyber threats are sophisticated, persistent, and often originate from within the network itself. This is where Zero Trust Architecture (ZTA) comes in — a security model that assumes no entity, internal or external, should be inherently trusted. Zero Trust enforces continuous verification of users, devices, and applications attempting to access resources, reducing the attack surface and strengthening enterprise security.
What is Zero Trust Architecture?
Zero Trust Architecture is a security framework that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are inside or outside the network perimeter. Unlike traditional models that automatically trust users inside the network, Zero Trust verifies every access attempt in real time.
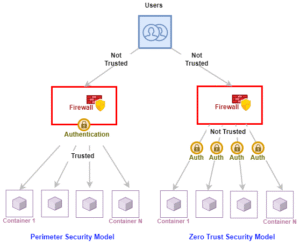
Figure 1: Traditional perimeter-based security vs. Zero Trust Architecture (Source: Guerna et al., 2023)
Key Principles of Zero Trust
- Verify explicitly: Always authenticate and authorize based on all available data points, including user identity, location, device health, and workload.
- Use least-privilege access: Limit user and device permissions to only what’s necessary for specific tasks.
- Assume breach: Design your systems as if attackers are already inside the network. Continuously monitor and analyze network activity for unusual behavior.
How IOTA Solutions Supports ZTA
IOTA Solutions offers a suite of security and network optimization products purpose-built for modern enterprise needs. Our key products include:
- iNAC: Enforces granular access control policies and real-time endpoint visibility, a cornerstone for Zero Trust implementation.
- Trace9: Provides deep network traffic monitoring and anomaly detection, enabling continuous verification and proactive threat management.
- Amygdala: An AI-driven behavioral security platform that detects abnormal user and device behavior within the network. It enhances ZTA by providing intelligent, adaptive risk scoring and automated response mechanisms to internal threats and advanced persistent threats (APTs).
Steps to Implement Zero Trust in Your Organization
- Identify sensitive data and resources.
- Map data flows and user interactions.
- Deploy identity and access management (IAM) solutions.
- Enforce multi-factor authentication (MFA).
- Implement continuous monitoring with AI-based analytics.
- Adopt micro-segmentation for limiting lateral movement.
- Integrate behavioral analytics tools like Amygdala for real-time threat detection.
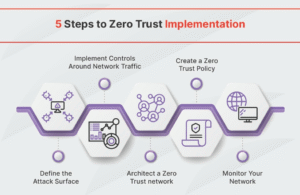
Figure 2: A visual framework for implementing Zero Trust, from defining protect surfaces to ongoing improvement. (Source: Fortinet)
Conclusion
Zero Trust isn’t a product but a strategy — one that requires coordinated implementation across identity management, access control, network monitoring, and endpoint security. With IOTA Solutions’ integrated platforms like iNAC, Trace9, and Amygdala, organizations can operationalize a Zero Trust Architecture that is adaptive, intelligent, and resilient against modern threats.
Author: Hassan Murad