Log Data Analysis
Amygdala XDR® provides log data analysis as one of its core module. This module enables your organization to collect, process, and analyze log data from a wide range of sources to gain insights into your system and network activity. Here’s an overview of how to log data analysis works in the Amygdala XDR®.
Amygdala XDR®’s log data analysis module uses an event-driven architecture that is designed to collect, normalize, and analyze log data from a wide range of sources. The architecture consists of the following components:
Data collectors
Amygdala XDR® supports a variety of data collectors for different log sources, including Amygdala XDR® agents, Syslog, and APIs. These collectors are responsible for gathering log data and sending it to the Amygdala XDR® manager.
Amygdala XDR® manager
The Amygdala XDR® manager is responsible for receiving, parsing, and storing log data in a centralized location. It also performs analysis of the log data using rules and correlation logic and generates alerts when potential security threats are detected.
Rules and correlation logic
Amygdala XDR® provides a wide range of pre-built rules and correlation logic that can be used to analyze log data and detect potential security threats. These rules can be customized to meet specific security needs.

Technical Description
Amygdala XDR® collects your log data from a variety of sources, including system logs, application logs, network devices, and cloud services and supports a wide range of log formats and provides pre-built decoders for common log types. It uses decoders to parse and normalize log data into a common format, making it easier to search, analyze, and correlate events across different sources. Amygdala XDR® provides a range of built-in rules and correlation logic to help you analyze log data and identify potential security threats. This includes detecting patterns of behavior that may indicate an attack, such as repeated login failures, unusual file access patterns, or suspicious network traffic.
Features
Centralized log management
With Amygdala XDR®, you can collect, normalize, and store log data from a wide range of sources in a centralized location. This can make it easier to manage and analyze security events across your entire environment.
Real-time analysis
Amygdala XDR®'s log data analysis engine analyzes your log data in real time, allowing you to detect potential security threats as they occur. This can help you respond to security incidents more quickly and effectively.
Advanced correlation
Amygdala XDR® uses advanced correlation techniques to identify patterns of behavior that may indicate a security threat. This includes cross-referencing log data from different sources to detect complex attacks that may span multiple systems or components. Overall, Amygdala XDR's log data analysis module provides a powerful way to manage and analyze security events across your environment. By centralizing log data and applying advanced correlation techniques, you can better detect and respond to potential security threats and improve your overall security posture.
Technology-Supported, Protocols
Amygdala XDR®’s log data analysis module supports a wide range of technologies and protocols for collecting and analyzing log data. Here are some of the key technologies and protocols that are used:
Syslog
Amygdala XDR® can collect and analyze syslog data from a variety of sources, including Unix/Linux systems, network devices, and applications.
Amygdala XDR® agents
Amygdala XDR® provides Amygdala XDR agents for Windows, Linux, and macOS that can collect and forward log data to the Amygdala XDR® manager for analysis.
APIs
Amygdala XDR® supports a variety of APIs that can be used to collect log data from third-party applications and services.
Amygdala XDR® Indexer
Amygdala XDR® uses Amygdala XDR® Indexer to store and search log data. Amygdala XDR® Indexer provides a fast and scalable way to store and search large volumes of data.
Logstash
Amygdala XDR® uses Logstash to collect, parse, and normalize log data from different sources. Logstash provides a flexible and extensible way to process log data before it is sent to Amygdala XDR® Indexer.
Pattern matching
Amygdala XDR® detects patterns of behavior that may indicate an attack, such as repeated login failures, unusual file access patterns, or suspicious network traffic.
Anomaly detection
Amygdala XDR® detects anomalous behavior by comparing log data to established baselines or statistical models. This can help identify new and emerging threats that may not be covered by the traditional rules-based analysis.
Cross-referencing
Amygdala XDR® can cross-reference log data from different sources to detect complex attacks that may span multiple systems or components.
Module Dependency
Amygdala XDR®’s log data analysis module depends on several libraries and projects to function properly. Here are some of the key dependencies:
Amygdala XDR® Indexer
Amygdala XDR®'s log data analysis module relies on Amygdala XDR® Indexer to store and search log data. Amygdala XDR® Indexer is an open-source search and analytics engine that provides a fast and scalable way to store and search large volumes of data.
Logstash
Amygdala XDR® uses Logstash to collect, parse, and normalize log data from different sources. Logstash is an open-source data processing pipeline that can be used to collect, process, and forward data.
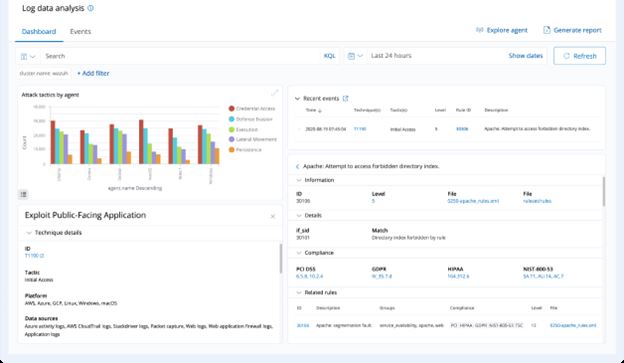
Amygdala XDR® Dashboard
Amygdala XDR®'s log data analysis module uses Amygdala XDR® Dashboard to visualize log data and create custom dashboards and reports. Amygdala XDR® Dashboard is an open-source data visualization solution that can be used to create interactive visualizations, such as charts, graphs, and tables.
OSSEC
Amygdala XDR®'s log data analysis module is based on the OSSEC project, which is an open-source host-based intrusion detection system. OSSEC provides a range of modules for analyzing system events and detecting potential security threats.
Logstash
Amygdala XDR® uses Logstash to collect, parse, and normalize log data from different sources. Logstash provides a flexible and extensible way to process log data before it is sent to Amygdala XDR Indexer.
OpenSCAP
Amygdala XDR®'s log data analysis module uses OpenSCAP to perform vulnerability assessments and compliance checks on systems. OpenSCAP is an open-source implementation of the Security Content Automation Protocol (SCAP) and provides a set of tools and libraries for assessing system security.
Suricata
Amygdala XDR®'s log data analysis module integrates with Suricata, which is an open-source network intrusion detection system. Suricata provides a range of modules for detecting and preventing network-based attacks.
Redefining IT Performance and Security Through Intelligent Innovation.
