Overview
Trace9® Monitoring solution collects, analyzes, and stores systems and application logs generated by various sources such as servers, applications, network devices, and security systems. Logs are records of events that occur in a system, and they contain information such as the time of the event, the type of event, the source of the event, and other relevant details. Nobody likes to keep making the same mistakes. Our Trace9® monitoring solution identify patterns to identify reoccurring issues and integrate check results, metrics, and logs in a single web interface, then use that extensive information to simplify your life.
Our Trace9® monitoring solution monitors, analyzes, and responds to system events in real-time. By collecting and analyzing log data, organizations can improve system performance, enhance security, and meet regulatory requirements
Features
Centralized Log Collection Trace9® Log Management module collects logs from different sources such as servers, applications, network devices, and cloud platforms, and stores them in a centralized location.
Log retention
Trace9® monitoring solution provides long-term log retention capabilities, which allows organizations to maintain a complete record of system activity over time. This can be useful for forensic analysis and trend analysis.
- Collects, measure, combine, and know with greater confidence.
- It gathers data and looks for trends in your log files and log management software.
- Collects and saves the measurements in time-series databases by using integrated writers, such as Elasticsearch.
- It observes log files or uses Elasticsearch to search log databases.
- Visualize your metrics stored in Graphite in the Trace9® Monitor interface.
- Use the rich set of templates or create your own.
- Display logs collected with the ELK stack in Trace9® Monitor.


Base Alerts on Metrics and Logs
With your collected data stored and structured it’s easy to automate checks and notifications. It detect problems automatically and stay in the loop.
- Trace9® Monitoring solution creates special checks for metrics and logs that trigger alerts based on the results.
- Creates notification rules on any metric or log stream.
- Trace9® Monitoring solution takes all the available data into account for alerting.
- Always stay informed and confident at any time.
Real-time Monitoring
Trace9® Log Management module provides real-time monitoring of logs allows IT teams to detect issues as soon as they occur, investigate their root cause, and take proactive measures to prevent future occurrences.
Advanced Search Capabilities
Trace9® Log Management module provides advanced search capabilities that enable IT teams to search logs across multiple sources using keywords, filters, and regular expressions.
Correlation and Analytics
Trace9® Log Management module correlates log data from different sources and performs analytics to identify patterns, anomalies, and trends. This capability can help IT teams gain insights into the overall health and performance of the infrastructure.
Alerting and Notification
Trace9® Log Management module generates alerts and notifications based on predefined conditions, such as error messages, critical events, or security breaches. This feature enables IT teams to take immediate action in response to critical events.
Compliance and Auditing
Trace9® Log Management module provides auditing and compliance capabilities, allowing IT teams to track and report on access to sensitive data, changes to configurations, and other activities.
Benefits
Improved security
Trace9® monitoring solution enables security teams to monitor and analyze system logs to detect security threats and vulnerabilities. By tracking and analyzing system logs, security teams can identify unusual activity and respond to potential security breaches in a timely manner.
Enhanced troubleshooting
Trace9® monitoring solution allows IT teams to quickly identify the root cause of system issues by analyzing log data. This can help reduce downtime and minimize the impact of system outages on business operations.
Compliance and auditing
Trace9® monitoring solution can help organizations meet regulatory requirements by providing an audit trail of system activity. By keeping a record of all system activity, organizations can demonstrate compliance with regulations and industry standards.
Centralized log storage
Trace9® monitoring solution provides a centralized location for storing logs from multiple sources, which makes it easier for IT teams to manage log data and quickly retrieve relevant information.
Real-time alerts
Trace9® monitoring solution generates real-time alerts based on predefined criteria. This can help IT teams quickly identify and respond to critical system events.
Improved performance
Trace9® monitoring solution enables IT teams to monitor system performance and identify areas for improvement. By analyzing log data, IT teams can identify performance bottlenecks and optimize system performance.
Technology Supported, Protocols, Devices
There are various technologies, protocols, and devices available for Trace9® Log management. Here are some examples:
- Log management software: These are software tools designed to collect, store, and analyze logs generated by various systems and devices. Some popular log management software tools include Splunk, Logstash, Graylog, and ELK Stack.
- SNMP: Trace9® monitoring solution supports SNMP (Simple Network Management Protocol) used for monitoring and managing network devices. It also collects logs from devices such as routers, switches, and firewalls.
- SIEM: Security Information and Event Management (SIEM) is a technology that combines log management with security information and event management. It provides a centralized view of security events and can detect and respond to security threats.
- Log collectors: Trace9® monitoring solution supports log collectors, devices that are installed on servers or network devices to collect and forward logs to a central log management system. Examples of log collectors include rsyslog, syslog-ng, and Fluentd.
- Cloud-based log management services: Trace9® monitoring solution supports Cloud-based log management services such as AWS CloudWatch, Google Cloud Logging, and Azure Log Analytics provide a scalable and cost-effective way to collect, store, and analyze logs in the cloud.
Module Dependency
To implement Trace9® log management effectively, you will need to consider the following module dependencies:
Log collection module
This module is responsible for collecting log data from various sources, including servers, applications, and network devices. It may use various log collection protocols such as syslog, SNMP, or agents to collect log data.
Log parsing and normalization module
This module is responsible for parsing log data and normalizing it into a consistent format so that it can be easily analyzed and correlated with other log data. It may also perform data enrichment, such as adding metadata and contextual information to the log data.
Log storage module
This module is responsible for storing log data in a centralized location, such as a log database or a data lake. It should be able to handle large volumes of data and provide fast retrieval and search capabilities.
Log analysis module
This module is responsible for analyzing log data to identify patterns, trends, and anomalies that may indicate issues or potential security threats. It may use various techniques such as machine learning, anomaly detection, and correlation analysis to identify issues.
Alerting and notification module
This module is responsible for alerting system administrators or other stakeholders when log data indicates an issue or potential security threat. It may use various notification channels such as email, SMS, or slack to notify stakeholders.
In conclusion, Trace9® monitoring solution has all these modules working together seamlessly to provide comprehensive log management capabilities which helps organizations monitor their infrastructure effectively.
Scalability
Trace9® Log management can be scaled to a considerable extent by using various techniques and technologies. Here are some examples:
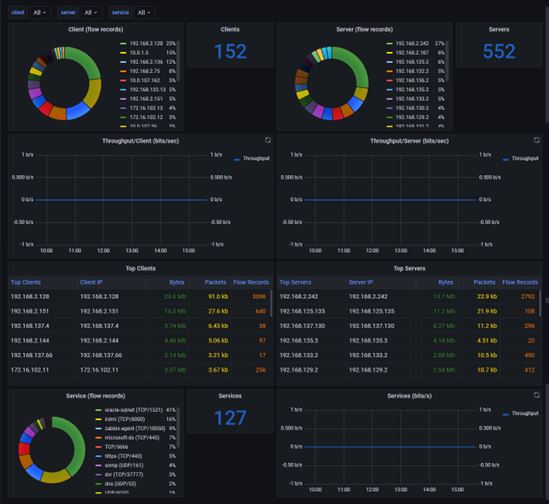
- Distributed Architecture
Trace9® Monitoring solution is designed with a distributed architecture that allows software to scale horizontally by adding more servers or nodes to handle the increased log volume.
- Cloud-Based Solutions
Trace9® Cloud-based log management services offer virtually infinite scalability as they can scale up or down as needed based on demand, without requiring upfront capital expenditure for additional hardware.
- Data Retention Policies
Trace9® defines data retention policies that specify how long logs should be kept before they are deleted or archived, and can help to reduce the overall amount of data that needs to be stored and managed.
- Automated Log Rotation
Trace9® Automated log rotation can also help to manage log data growth by automatically archiving or deleting older logs based on predefined rules.
- Data Compression
Trace9® compress log data can help to reduce the amount of storage required while still retaining the ability to search and analyze the data.
Trace9® editions difference table
This edition difference table Provides a comparison between different editions of Trace9® Monitoring Solution. It outlines the features, content, or specifications that distinguish one edition from another. The edition table helps customers make informed decisions about which edition best suits their needs or preferences.
| Trace9® Modules | Trace9® Standard | Trace9® Professional | Trace9® Advanced | Enterprise | Service Provider | |
|---|---|---|---|---|---|---|
| Legend | x = Supported - NS= Not Supported "Version upgrade will require" | |||||
| Trace9® Satellite Node | ||||||
| Network Performance Monitor (NPM) | ||||||
| NPM IOT Monitor | ||||||
| Desktop & Application Monitor | ||||||
| Server & Application Monitor | ||||||
| Virtualization Monitor | ||||||
| Database Monitor | ||||||
| Cloud Monitoring | ||||||
| HCI Monitor | NS | |||||
| Advanced Virtualization Monitor | NS | |||||
| Log Management | NS | |||||
| Software License Monitoring | NS | NS | ||||
| ITSM Integration | NS | |||||
| Network xFlow | NS | |||||
| NF Virtualization Monitor | NS | NS | ||||
| SD-WAN Performance Monitor | NS | |||||
| Trace9® Special Integration Packs-Telco | NS | NS | NS | NS | ||
Redefining IT Performance and Security Through Intelligent Innovation.
