Harness the power of AI and innovation with iOTA Solutions’ advanced monitoring platforms. Trace9®, our unified monitoring platform, uses AI to monitor your entire IT stack, ensuring service continuity and proactive insights to keep your business running smoothly. Amygdala XDR®, our intelligent security monitoring solution, protects your organization with real-time, AI-powered threat detection and alerts, keeping you one step ahead of cyber risks. iNAC, our AI-enhanced network access control solution, gives you full command over who can access your internal network, offering features like a captive portal, centralized management of wired, wireless, and VPN connections, and industry-leading BYOD support. Transform your IT and security operations with iOTA Solutions’ AI-centric approach to proactive monitoring.



Why Choose Us
Unleash the power of innovation and collaboration with IOTA Solutions. Our unique selling point lies in our ability to seamlessly blend cutting-edge technology with the specific customer needs.
- Unification and Correlation, Monitoring solutions providing holistic visibility across multiple technologies and services.
- Cut to fit Simplified Licensing Model, Transparent simplified licensing giving customers the control and visibility of TCO for their investments.
- Use Case Driven Framework, Supported by DevOps practice, customer use cases are adapted to deliver cut-to-fit monitoring solutions
- Based on Open and Robust Platform, Data-driven, intelligent, and adaptive platforms on open and robust foundations for our customers.
- The Team, 360-degree organizational experience. 50+ recourses ranging from consulting, development, system integration to operations across all domains.
Our solutions and services are created on the back of expertise in IT, Data Centers, Service delivery and operations. This knowledge is reflected in the solutions which are personalized and not just off-the-shelf products.
- We support all deployment options i.e., on premises, cloud and hybrid based on the use cases and needs.
- IOTA Solutions Framework (ISF), assisting customers in achieving organizational goals in accordance with business requirements.
- The solutions give you cost optimized options to cover your complete multi-technology stack, hence provide the complete service-level visibility at a unified layer.
Unlock a competitive edge with solutions powered by cutting-edge AI and cognitive technologies, delivering insights that fuel innovation tailored to market and customer needs.
Your critical infrastructure holds valuable data about network behavior. Our solutions, driven by advanced Machine Learning and AI algorithms, interpret this data to provide actionable intelligence, ensuring seamless operations and service continuity.
With open platforms, you gain the freedom to integrate and customize without limitations, enabling rapid time-to-market and safeguarding your investments. Our delivery model is centered on your success, offering comprehensive support through flexible licensing, tailored training, DevOps integration, and dedicated services.
Trace9®
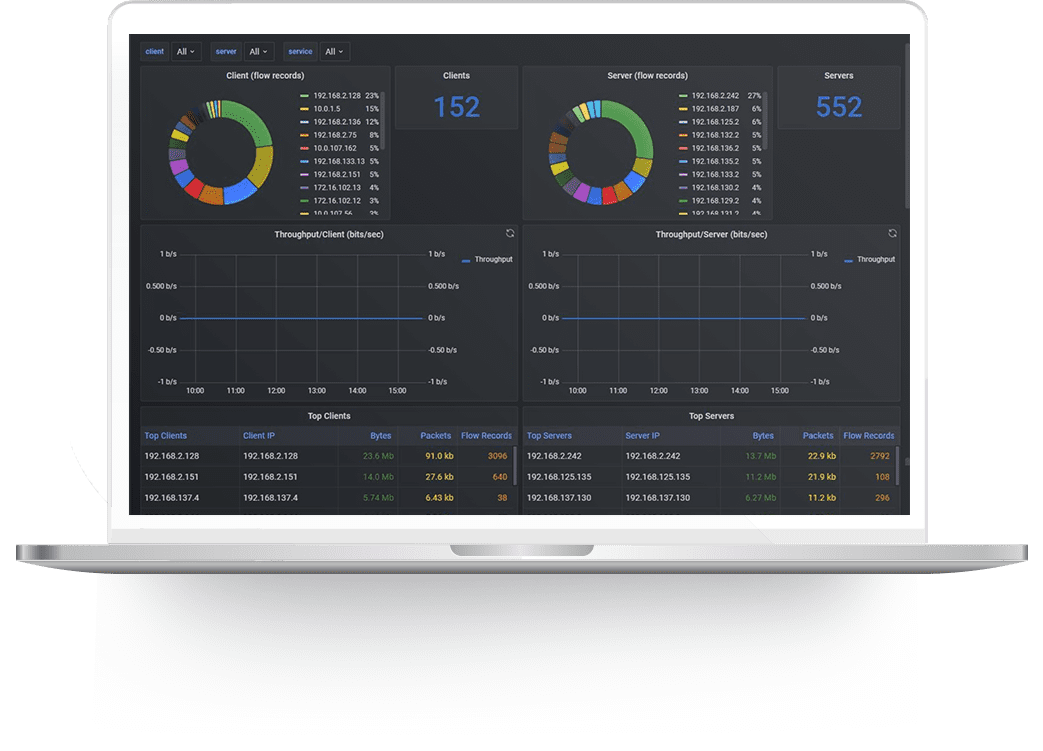
Trace9® – The Ultimate Unified IT Monitoring Solution
Trace9® – A unified solution that monitors and manages the health and performance of the entire IT infrastructure across physical, virtual, and hybrid IT environments. It enables organizations to keep track of and observe the performance of their networks, servers, databases, cloud, and all other IT assets in their environment. Get a unified 360-degree monitoring view for complete enterprise IT infrastructure, break down silos and accelerate your business.
Edition Choice
Trace9® offers multiple editions available for customers who need to monitor and manage their own IT infrastructure and applications. You can select the edition that best suits your IT monitoring needs and budget. Also you can select the licensing type (perpetual or subscription) that matches your total cost of ownership (TCO).
Modular Approach
Trace9® employs a modular approach to provide flexibility, scalability, and extensibility for our valuable customers. This approach provides a comparison between different modules of the Trace9® Monitoring Solution. It outlines the features and specifications that distinguish one modular from another. It helps customers make informed decisions about which module best suits their needs or preferences.
Multi-tenant Architecture for MSPs
Trace9® monitors multiple customer’s IT environments from a single dashboard with customer-specific dashboards, alerts and reports.
Usecase Driven
We don’t just offer one-size-fits-all solutions, Trace9®’s use case driven approach addresses the specific needs and pain points of our valuable customers, creating a customized and tailored solution.
Amygdala XDR®
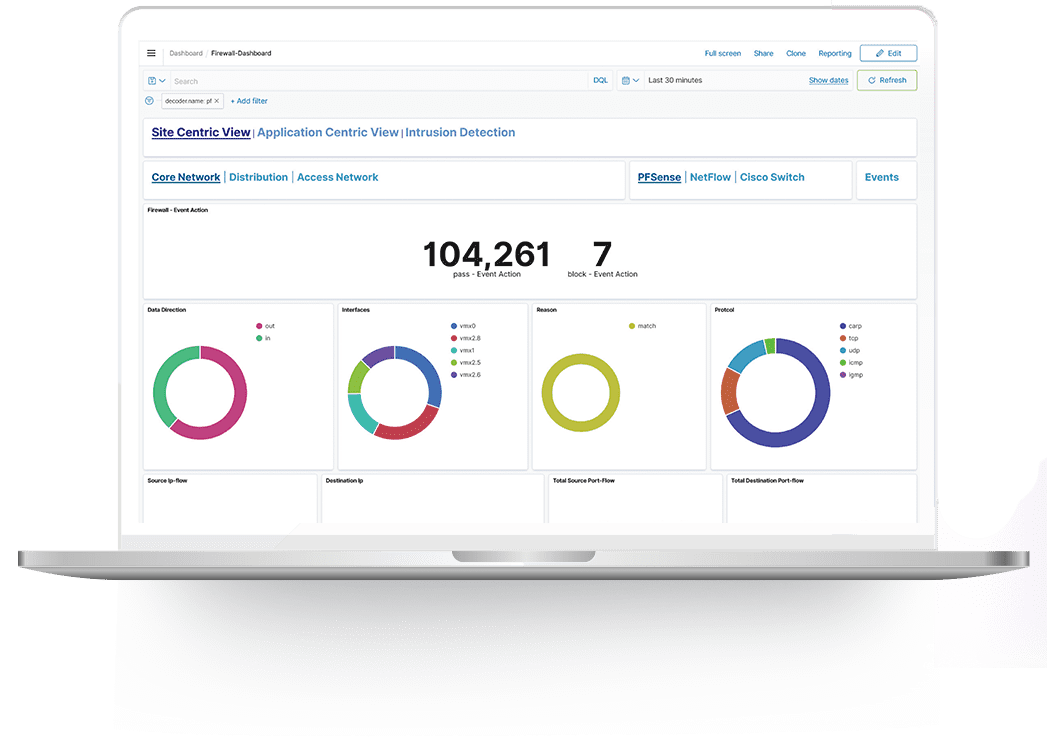
Amygdala XDR® – Extended Detection, Response & Compliance Monitoring Solution
Amygdala XDR® is security detection, visibility, and compliance platform that enables organizations to protect their IT infrastructure from potential threats and actively respond to security threats in real-time. It provides centralized logging and analysis of security events across an organization’s IT infrastructure, including servers, endpoints, cloud environments, containers, and networks.
Real-time Threat Detection
Amygdala XDR® detects all known and unknown security threats in real-time, by analyzing security events and logs from across an organization’s IT infrastructure.
Incident response
Amygdala XDR® incident response capabilities allow security teams to respond to incidents quickly and effectively, reducing the impact of the attack.
Integration with other security tools
Amygdala XDR® integrates with other security tools, including IDS/IPS, vulnerability scanners, and SIEM solutions, providing a holistic security solution.
Compliance monitoring
Amygdala XDR® offers compliance monitoring capabilities that assist organizations in ensuring that they meet the best industry and regulatory standards.

iNAC
iNAC – Comprehensive, scalable, security solution
Build a stronger network defense with iNAC! Just like a building block system, it secures your data with access control, threat detection, and device isolation. Manage BYOD devices seamlessly. iNAC: The easy-to-use, comprehensive security solution that keeps your business running smoothly.
Network Access Control
iNAC serves as a gatekeeper for your network, offering strong access management. It acts as a strategic enforcer of network security protocols, ensuring that only vetted users and devices gain entry. This fortifies your network’s defenses and supports regulatory compliance.
Anomaly Detection
iNAC’s vigilant monitoring system acts as an early-warning radar for unusual network patterns. By alerting your IT team to potential security breaches, it enables a swift response, safeguarding your network’s operational integrity.
BYOD Management
In today’s mobile-first world, iNAC’s comprehensive BYOD management tools are essential. They provide a framework for personal devices to integrate seamlessly and securely with corporate network policies, balancing flexibility with control.
Vulnerability Scanning
With iNAC’s continuous vulnerability assessment, your network undergoes thorough scrutiny, identifying and allowing for the remediation of security gaps. This preemptive scanning is key to maintaining a resilient network.
Device Isolation
iNAC’s capability to quarantine suspect devices is akin to an immune response, isolating threats to prevent network contamination. This ensures that a single compromised device doesn’t escalate into a full-blown network crisis.
Our Success Story


































Case Studies




Redefining IT Performance and Security Through Intelligent Innovation.

